CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
$149.99$275.00
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Entire Course
CIS 105 Capstone Discussion Question
CIS 105 Assignment: Technology of the Future
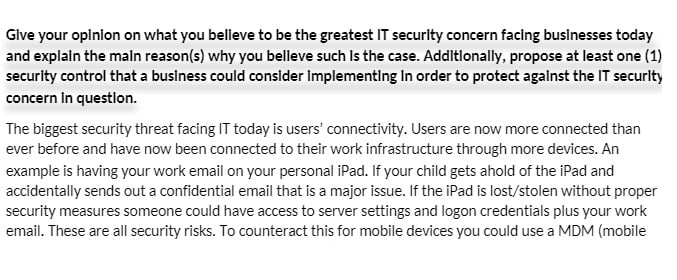
CIS 105 Assignment: Security Systems
CIS 105 CheckPoint: Internet Scavenger Hunt
CIS 105 CheckPoint: Computer Comparison
CIS 105 CheckPoint: Data Versus Information
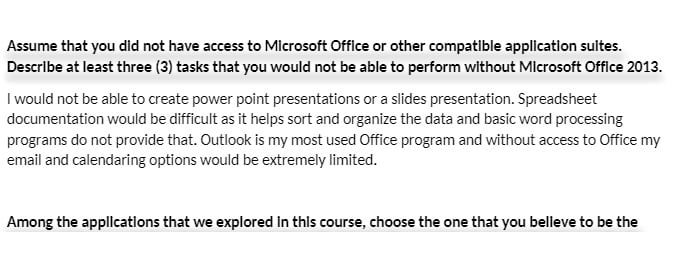
CIS 105 CheckPoint: Microsoft® Word
CIS 105 CheckPoint: Types of Networks
CIS 105 CheckPoint: Cyber Security
CIS 105 Assignment: PowerPoint®
CIS 105 CheckPoint: Formatting Excel Spreadsheets
CIS 105 Assignment: Manipulating Data in Excel Spreadsheets
CIS 105 Week 1 DQ 1
CIS 105 Week 1 DQ 2
CIS 105 Week 3 DQ 1
CIS 105 Week 3 DQ 2
CIS 105 Week 5 DQ 1
CIS 105 Week 5 DQ 2
CIS 105 Week 7 DQ 1
CIS 105 Week 7 DQ 2
CIS 105 Final Multimedia Tools in the Classroom
Description
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Entire Course
CIS 105 Capstone Discussion Question
CIS 105 Assignment: Technology of the Future
CIS 105 Assignment: Security Systems
CIS 105 CheckPoint: Internet Scavenger Hunt
CIS 105 CheckPoint: Computer Comparison
CIS 105 CheckPoint: Data Versus Information
CIS 105 CheckPoint: Microsoft® Word
CIS 105 CheckPoint: Types of Networks
CIS 105 CheckPoint: Cyber Security
CIS 105 Assignment: PowerPoint®
CIS 105 CheckPoint: Formatting Excel Spreadsheets
CIS 105 Assignment: Manipulating Data in Excel Spreadsheets
CIS 105 Week 1 DQ 1
CIS 105 Week 1 DQ 2
CIS 105 Week 3 DQ 1
CIS 105 Week 3 DQ 2
CIS 105 Week 5 DQ 1
CIS 105 Week 5 DQ 2
CIS 105 Week 7 DQ 1
CIS 105 Week 7 DQ 2
CIS 105 Final Multimedia Tools in the Classroom
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Capstone Discussion Question
Capstone Discussion Question
· Due Date: Day 3 [Main forum]
· Post your response to the following: What did you learn from this course that is new and
helpful to you? How will you use that information in the future? What useful advice could
you provide someone based on what you have learned?
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Assignment: Technology of the Future
Assignment: Technology of the Future
· Resources: Ch. 5 in Computing Fundamentals and the HowStuffWorks Web site
· Due Date: Day 7 [Individual forum]
· Read Ch. 5 (pp. 206-217) in Computing Fundamentals, which explains that the potential
for computers to process information faster and become exponentially more powerful
seems limitless.
· Think about the current capabilities of computer technology to what was thought
impossible ten years ago. What are the possibilities for the use of technology in the near
and distant future?
· Access the HowStuffWorks Web site at http://www.howstuffworks.com/ to explore the
possibilities. Type in a new or future technology in the search window to discover a world
of possibilities.
· Describe one technological device in 350 to 700 words. Include the following: When did
it come (or will it potentially come) into existence? What scientific or technological
reasoning explains how this potential has been (or can be) be reached?
· Format the paper and any citations of additional resources according to APA guidelines.
· Post the assignment as an attachment.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Assignment: Security Systems
Assignment: Security Systems
· Resources: Symantec, McAffee, SonicWALL Web sites
· Due Date: Day 7 [Individual forum]
· Research two available security systems that provide total network protection, also
known as all-in-one computer security systems.
· Refer to Web sites such as Symantec at http://www.symantecstore.com/v2.0-
img/operations/symantus/site/promo/pd/pt-navnis360-us.html, McAffee at
http://shop.mcafee.com/Default.aspx, and SonicWALL at
http://www.sonicwall.com/emea/5609.html
· Explain the following in 350 to 700 words: How do computers benefit from having all-inone
computer security systems installed? What makes them effective? What do they
protect against?
· Format the paper and any citations of additional resources according to APA guidelines.
· Post the assignment as an attachment.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 CheckPoint: Internet Scavenger Hunt
CheckPoint: Internet Scavenger Hunt
· Resource: Appendix B
· Due Date: Day 5 [Individual forum]
· Choose a topic related to computer technology that interests you. Possible subjects can
be gleaned from your text.
· Narrow the topic to a specific search. If you are interested in available storage devices,
for example, narrow your topic to a particular item such as a USB flash drive.
· Write a statement in Appendix B next to Search Statement that explains exactly what you
are searching for, then complete the following steps:
o Decide which keywords from your statement to use for your search. Use at least two
and record them in Appendix B next to Search Keywords.
o Choose three search engines from which to begin your research, such as
google.com, yahoo.com, live.com, ask.com, and lycos.com. You may choose from
this list or find your own.
o Create hyperlinks to each search engine in Appendix B. To create this hyperlink:
1. Access a site.
2. Highlight the Web address in the address box.
3. Copy (Ctrl + C) the address.
4. Paste (Ctrl + V) the address into Appendix B next to search engine 1, 2, or 3.
CIS 105 Survey of Computer Information Systems
Course Syllabus Page 14
o Open the search engine by clicking on its URL. Insert the keywords into the
appropriate box and press the Enter key. Record the number of results as well as the
top three Web links listed for each of your searches in Appendix B. It may be easiest
to highlight, then copy and paste the corresponding URLs directly into Appendix B.
o Using the same keywords, conduct two more searches each with a different search
engine.
o Conduct another set of searches with the same keywords, but using a Boolean such
as and, or, or not. Note: Different search engines may use different words or symbols
for the Boolean searches. You need to find out how to do this with each search
engine.
o Note the number of results for each of your Boolean searches and record it in
Appendix B.
· Summarize by answering the following questions in 100 to 350 words:
o What are some of the advanced search options available with each search engine?
o What other services beside the search engine does each site offer?
o What did you like about each search engine? What did you not like?
o Which of the three search engines did you find the most effective? Why?
o Why do you think the use of Booleans did or did not affect the number of results
returned by the search engines?
· Complete the matrix in Appendix B.
· Post your 100- to 350-word summary in the Individual forum with Appendix B as an
attachment.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 CheckPoint: Computer Comparison
CheckPoint: Computer Comparison
· Resources: Ch. 1 (pp. 27-32) of Computing Fundamentals and PCWorld and Macworld
Web sites
· Due Date: Day 5 [post to the Individual forum]
· Read pp. 27-32 of Ch.1.
· Think about how your computer system compares to a state-of-the-art system.
CIS 105 Survey of Computer Information Systems
Course Syllabus Page 11
· Identify the following components of your system: type of central processing unit (CPU),
amounts of random access memory (RAM) and read-only memory (ROM), input and
output devices, and types of storage.
· Compare these elements to new, state-of-the art technology available. To aid your
research, use links to online stores such as the following: PCWorld at
http://www.pcworld.com/ and Macworld at http://www.macworld.com/
· Write a 350- to 700-word paper.
· Cite any additional resources you reference in APA format.
· Post the paper as an attachment.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 CheckPoint: Data Versus Information
CheckPoint: Data Versus Information
· Resource: Ch. 5 in Computing Fundamentals
· Due Date: Day 4 [Individual forum]
· Consider the following: Computers use a completely different language than people, yet
they communicate effectively with people.
· Refer to Ch. 5 in Computing Fundamentals.
· Distinguish between computer data represented by the state of a computer’s electrical
switches and the meaningful information that is displayed to the user.
· Write a 200- to 350-word paper that describes the distinctions of data and information
and briefly explains the process a computer uses to convert data into information.
· Cite any additional resources you reference in APA format.
· Post the CheckPoint as an attachment.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 CheckPoint: Microsoft® Word
CheckPoint: Microsoft® Word
· Resource: pp.303-307 in Computing Fundamentals and the Computer Applications
Tutorial
· Due Date: Day 4 [Individual forum]
· Refer to pp.303-307 in Ch. 8 of Computing Fundamentals.
· Complete the Word portion of the Computer Applications Tutorial and manipulate a document using the
word processing program on your computer with the following specifics:
o Open Microsoft® Word.
o Create a new document by clicking on File, then New.
o Copy and paste the following paragraph:
1. Click and move your mouse over the paragraph, highlighting the paragraph.
2. Click Ctrl + C (copy).
3. Click on your blank document with the mouse.
4. Click Ctrl + V (paste).
Learning how to use Word to improve personal and job productivity is easy and helpful.
The basics include opening and creating a Word document, making the document appear
professional, and saving the file.
· Complete the following changes on this paragraph:
o Before you lose any data, click on File, Save As, and name this file
yournameweek4checkpoint, such as karenweek4checkpoint.
o Use Ctrl + S to save the file every minute to avoid losing data.
o Add one line to the paragraph above about how hard or easy you found this process
to be by clicking at the end of the last sentence and typing.
o Move your mouse over the first sentence, highlighting the sentence.
o Move your mouse up to the toolbar at the top of the page and click on the “B” to bold
the sentence.
o Click and move your mouse over the second sentence, highlighting the sentence.
o Move your mouse up to the toolbar at the top of the page and click on the “A” to
change the color of the second sentence to blue.
o Click and move your mouse to highlight the entire paragraph.
o Click on Format on the toolbar, Font, and change the font to 14-pt Comic Sans, and
then click OK.
o Click on the paragraph at the start of the first line with your mouse and hit Tab to
indent five spaces.
CIS 105 Survey of Computer Information Systems
Course Syllabus Page 16
· Save document and post it as an attachment.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 CheckPoint: Types of Networks
CheckPoint: Types of Networks
· Resource: Ch. 9 (pp. 346-347) in Computing Fundamentals
· Due Date: Day 5 [Individual forum]
· Refer to Ch. 9 (pp. 346-347) in Computing Fundamentals.
· Compare and contrast LANs, WANs, CANs, MANs, and HANs in 200 to 350 words.
· Cite any additional resources used in APA format.
· Post the CheckPoint as an attachment.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 CheckPoint: Cyber Security
CheckPoint: Cyber Security
· Resource: Ch. 12 in Computing Fundamentals
· Due Date: Day 4 [Individual forum]
· Read the following scenario:
James was traveling for his job. The internet card provided by his company was not
working and he had an important project due that day. James was in a small town about
an hour away from the nearest internet kiosk, so he decided to drive around a nearby
suburb to see if he could find a wireless system he could “borrow” to send out his project.
James found a wireless system without a security key and, after parking near the home
with the system, uploaded the project. Afterward, just for fun, James peaked into the
computer on the wireless system and found, to his dismay, some bank accounts and
passwords.
· Think about how you would feel if James were parked outside your home, using your
wireless network.
· Refer to Ch. 12 in Computing Fundamentals
· Explain the following in 350 to 700 words: Before this class, what means, if any, were
you employing to protect yourself in the cyber world? What security measures are
available to the average computer user? What is missing from the system James
“borrowed?” Which do you think are most important? How might you change your
approach to online security in the future?
· Cite any resources used in APA format.
· Post the CheckPoint as an attachment
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Assignment: PowerPoint®
Assignment: PowerPoint®
· Resources: Ch. 8 (pp. 312-316) in Computing Fundamentals and the Computer
Applications Tutorial
· Due Date: Day 7
· Complete the PowerPoint® portion of the Computer Applications Tutorial then create a PowerPoint®
presentation for the following scenario:
You work for a large retailer of consumer electronics that is constantly seeking to add the
latest technologies to its product lines. Find one new electronics product that you think
the company should consider incorporating into its line of merchandise using resources
such as http://www.engadget.com/ and http://www.cnet.com/ and
http://www.pcworld.com/
· Create an 8- to 10-slide presentation for upper management that supports your decision.
Your goal is to convince the executive board to adopt this product.
You want to consider the following as you are creating your presentation:
o How does this new technology benefit consumers?
o Why would consumers want to buy this product?
o What makes this product better than other similar products?
o What features does this product include?
Your presentation must include the following components:
o A title slide for the first slide
o A reference slide for the final slide
o A slide design
o At least three different slide layouts
o At least one clipart to support the content of the presentation
o At least one picture to support the content of the presentation
o Detailed speaker notes
Your presentation must include the following modifications:
o Change the font of the title in the slide master.
o In the speaker notes of the first slide, make note of the font change. Be sure to make
this change after you have selected and applied your slide design.
o Insert your name in the footer area of the slide master.
· Post the presentation as an attachment.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 CheckPoint: Formatting Excel Spreadsheets
CheckPoint: Formatting Excel Spreadsheets
· Resource: Ch. 8 (pp. 308-311) in Computing Fundamentals, the Computer Applications
Tutorial and Appendix D
· Due Date: Day 4 [Individual forum]
· Refer to Ch. 8 (pp. 308-311) in Computing Fundamentals.
· Review the Excel portion of the Computer Applications Tutorial and explore the spreadsheet program
on your computer.
· Use the information available in Appendix D to format a Microsoft® Excel data set. The
scenario for this data set is as follows:
You just had a birthday a couple of weeks ago and you were somewhat surprised by
some of the presents you received, pleasantly in several cases and unpleasantly in
others. On a whim, you lightheartedly decide to find out who loves you the most based
upon the gifts you were given. You use a spreadsheet to analyze the information. For this
CheckPoint, you refine the spreadsheet, manipulating the document in the following
ways:
o Use at least two different font sizes.
o Change the font.
o Use at least one font style such as bold, italics, and underline.
o Apply color to at least one set of text.
o Apply a fill color to at least one set of cells.
o Apply a border to at least one group of cells.
o Format all cells with dollar amounts as currency.
o Use the fill handle to fill in the remaining cells in the Birthday column. Note: The fill
sequences the dates, so you need to choose the option to copy cells.
o Format all of the cells with dates as xx/xx/xxxx.
· Submit the spreadsheet as an attachment with the answers to the following questions as
a post of 50 to 100 words:
o What did you like about Excel?
o What seemed frustrating?
o What did you not understand?
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Assignment: Manipulating Data in Excel Spreadsheets
Assignment: Manipulating Data in Excel Spreadsheets
· Resources: Appendix D, Appendix E, and Appendix F
· Due Date: Day 7 [Individual forum]
CIS 105 Survey of Computer Information Systems
Course Syllabus Page 20
· Use the chart tutorial in Appendix E and Appendix F to familiarize yourself with creating
charts and graphs in Excel.
· Continue to manipulate the data in the Appendix D Excel spreadsheet from the previous
CheckPoint in the following ways:
o Use the sum function to find the total number of gifts and the total value of the gifts.
o Use the average function to find the average number of gifts per person and the
average value of the gifts per person.
o Use a formula to find the average cost per gift for Mom. Then, use the fill handle to fill
in that formula for the remaining friends and family.
o Use a formula to find the percentage of monthly income Mom spent on the gift. Then,
use the fill handle to fill in that formula for the remaining friends and family.
o Use a formula to find the number of days, early or late, Mom presented her gift. Then,
use the fill handle to fill in that formula for the remaining friends and family.
o Format the total value of gifts, average cost per gift, and monthly income columns as
currency.
o Format the % of monthly income spent on gifts column as percentages.
o Create at least one chart to illustrate your analysis.
· Submit the spreadsheet as an attachment with the answer to the following question as a
post of 100 to 350 words: Based on the information in this spreadsheet, which of your
friends or family do you think loves you the most? Use the data to justify your answer.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Week 1 DQ 1
Discussion Question 1
· Due Date: Day 2 [post to the Main forum]
· Post your response to the following: Think about how computer technology permeates
society. Throughout the day, you encounter many types of computerized devices at the
grocery store, fast food chains, school, and work. Describe one such device available
today: Who uses it, what are they able to accomplish with its use, and how do people
benefit from its existence?
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Week 1 DQ 2
Discussion Question 2
· Due Date: Day 4 [post to the Main forum]
· Post your response to the following: As you have discovered, there are a variety of
computers available, from the smallest computer in a domestic device to the
supercomputers used in industry. Despite the different uses of computers, they all have
basics elements in common—each computer system involves hardware, software, data,
and users. Think about the role of each component of your home or work computer: How
do the components of your computer system interact within the system? What
improvements or additions to your system do you think would benefit you or make the
system more user-friendly? Why?
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Week 3 DQ 1
Discussion Question 1
· Due Date: Day 2 [Main forum]
· Post your response to the following after considering how technology enables people to
communicate constantly with each other through mobile phones, instant messaging,
video teleconferencing, and e-mail: How often do you gain or exchange information via
your computer? In how many ways is this possible? How valuable do you think the
internet has become to personal communication? What are some of the problems that
sometimes arise through the use of this technology? How could it affect a learning
environment?
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Week 3 DQ 2
Discussion Question 2
· Due Date: Day 4 [Main forum]
· Post your response to the following: How does electronic commerce (e-commerce) affect
you as a consumer, and how do you think e-commerce affects the way companies do
business?
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Week 5 DQ 1
Discussion Question 1
· Due Date: Day 2 [Main forum]
· Post your response to the following after exploring one or more graphic programs
available on your computer: Share your experience with the class. What did you like and
dislike about the program? What advice could you give someone using the program for
the first time?
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Week 5 DQ 2
Discussion Question 2
· Due Date: Day 4 [Main forum]
· Post your response to the following after exploring Web sites such as
http://www.foxnews.com/. After visiting several similar sites, what is one example of a
computer based non-interactive multimedia? What is one example of an interactive
multimedia? What are some of the advantages that interactive multimedia has over noninteractive
multimedia? How might interactive multimedia benefit education? Be sure to
cite specific examples.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Week 7 DQ 1
Discussion Question 1
· Due Date: Day 2 [Main forum]
· Post your response to the following: Most personal computers come equipped with a
version of the Windows operating system, whereas Apple personal computers have a
different operating system. Other choices are also available, such as UNIX and Linux.
Why do you think Windows is so prevalent? What do the other systems have to offer that
Windows does not? Who uses the other systems?
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Week 7 DQ 2
Discussion Question 2
· Due Date: Day 4 [Main forum]
· Post your response to the following: What is the importance of an operating system
(OS)? What reasons would a computer user have to change from one OS to another?
What do you like and dislike about the OS on your computer at home or at work? Explain
why.
CIS 105 CIS105 CIS/105 ENTIRE COURSE HELP – STRAYER UNIVERSITY
CIS 105 Final Multimedia Tools in the Classroom
CIS 105 Final Multimedia Tools in the Classroom