CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
$3.99
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
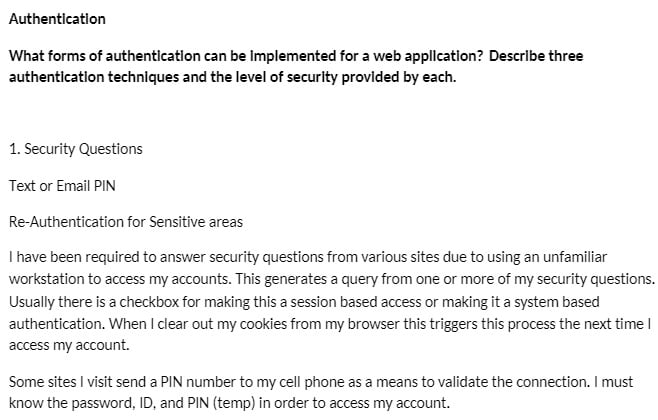
Authentication
What forms of authentication can be implemented for a web application? Describe three authentication techniques and the level of security provided by each.
1. Security QuestionsText or Email PINRe-Authentication for Sensitive areas
I have been required to answer security questions from various sites due to using an unfamiliar workstation to access my accounts. This generates a query from one or more of my security questions.
Usually there is a checkbox for making this a session based access or making it a system based authentication.
Description
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
Authentication
What forms of authentication can be implemented for a web application? Describe three authentication techniques and the level of security provided by each.
1. Security QuestionsText or Email PINRe-Authentication for Sensitive areas
I have been required to answer security questions from various sites due to using an unfamiliar workstation to access my accounts. This generates a query from one or more of my security questions.
Usually there is a checkbox for making this a session based access or making it a system based authentication. When I clear out my cookies from my browser this triggers this process the next time I access my account.Some sites I visit send a PIN number to my cell phone as a means to validate the connection.
I must know the password, ID, and PIN (temp) in order to access my account.I also have a work WebVPN account that uses an RSA token based PIN number. Part of that PIN is something I know and the other part is a synchronized random number that is displayed on the token.
I must know my part and possess the token to get the second part. I must also know my login ID. This presents I believe a very high level of security for my account. Two things I know, ID, PIN and one thing I must possess, RSA Token PIN.
2. Authentication is the process that verifies whether a user is the one whom they claim themselves to be and not a pretender.
There are several ways of web application authentication that can be implemented such as single or basic authentication, and multi layered authentication. The techniques used to authenticate can be:
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
CMIT 321 Ethical Hacking School: University of Maryland University College (UMUC) *Professor:Christopher J Gripko, kevincardwell, DavidMashburn, Daston,Mel… Documents (1293) Q&A (74) Textbook Exercises
Most important docs of the week 4 pagesReconnaissance Plan and Scanning Plan 3 UMUC.docxReconnaissance Plan and Scanning Plan 3 UMUC.docx University of Maryland, University College
CMIT 321 – Fall 2020 Register Now Reconnaissance Plan and Scanning Plan 3 UMUC.docx 2 pagesReconnaissance Plan and Scanning Plan.docxReconnaissance Plan and Scanning Plan.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2019 Register Now Reconnaissance Plan and Scanning Plan.docx 4 pagesReconnaissance Plan and Scanning Plan.docxReconnaissance Plan and Scanning Plan.docx University of Maryland, University College
CMIT 321 – Fall 2020 Register Now Reconnaissance Plan and Scanning Plan.docx 3 pagesKyle_Jackson_Reconnaissance Plan and Scanning Plan.docxKyle_Jackson_Reconnaissance Plan and Scanning Plan.docx University of Maryland, University College
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
CMIT 321 – Fall 2019 Register Now Kyle_Jackson_Reconnaissance Plan and Scanning Plan.docx 4 pagesReconnaissancePlanandScanningPlanTemplate1-1.docxReconnaissancePlanandScanningPlanTemplate1-1.docx University of Maryland, University College
CMIT 321 – Fall 2019 Register Now ReconnaissancePlanandScanningPlanTemplate1-1.docx Ethical Hacking Documents All (1293) Assignments (1) Essays (75) Homework Help (253) Lab Reports (271) Notes (113)
Test Prep (99) Showing 1 to 30 of 1,293 Sort by: Most Popular 8 pagesCMIT321QUIZ2.pdfCMIT321QUIZ2.pdf University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now CMIT321QUIZ2.pdf 2 pagesWeek 4Week 4 University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2015 Register Now Week 4 2 pagesRules of Engagement Template.docxRules of Engagement Template.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Spring 2020 Register Now Rules of Engagement Template.docx 1 pagesWeek 3Week 3 University of Maryland, University College Ethical Hacking
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
CMIT 321 – Fall 2015 Register Now Week 3 5 pagesAYANNA EXEC. PROPOSAL.docxAYANNA EXEC. PROPOSAL.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2019 Register Now AYANNA EXEC. PROPOSAL.docx 6 pagesDeliverable 1- Rules of Engagement.docxDeliverable 1- Rules of Engagement.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now Deliverable 1- Rules of Engagement.docx 5 pagesAuthentication.docxAuthentication.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now Authentication.docx 22 pagesCMIT 321 FINAL EXAM.docxCMIT 321 FINAL EXAM.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2019 Register Now CMIT 321 FINAL EXAM.docx 4 pagesPenetration Test Proposal-.docxPenetration Test Proposal-.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2019 Register Now Penetration Test Proposal-.docx 69 pagesSmith_CEHv9lab5.docxSmith_CEHv9lab5.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2019 Register Now Smith_CEHv9lab5.docx 3 pagesQuiz 3Quiz 3 University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now Quiz 3 4 pagesROE – TRidgeway.docxROE – TRidgeway.docx University of Maryland, University College
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
CMIT 321 – Fall 2020 Register Now ROE – TRidgeway.docx 4 pagesReconnaissance Plan and Scanning Plan.docxReconnaissance Plan and Scanning Plan.docx University of Maryland, University College
CMIT 321 – Fall 2020 Register Now Reconnaissance Plan and Scanning Plan.docx 5 pagescmit321 project proposal.docxcmit321 project proposal.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2017 Register Now cmit321 project proposal.docx 2 pagesRules of Engagement Proposal.docxRules of Engagement Proposal.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2019 Register Now Rules of Engagement Proposal.docx 1 pagesWeek 1 Discussion Questions.docxWeek 1 Discussion Questions.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now Week 1 Discussion Questions.docx 2 pagesCMIT 321 Week 1 Discussion ECMIT 321 Week 1 Discussion E University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now CMIT 321 Week 1 Discussion E 4 pagesiLab Screen Shots (Modules 16 and 17)iLab Screen Shots (Modules 16 and 17) University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now iLab Screen Shots (Modules 16 and 17) 1 pagesCMIT321 Week 4 Discussions BCMIT321 Week 4 Discussions B University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now CMIT321 Week 4 Discussions B 18 pagesCMIT 321 – Lab 2CMIT 321 – Lab 2 University of Maryland, University College Ethical Hacking
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
CMIT 321 – Fall 2016 Register Now CMIT 321 – Lab 2 10 pagesCMIT 321 week 4 labsCMIT 321 week 4 labs University of Maryland, University College
CMIT 321 – Spring 2016 Register Now CMIT 321 week 4 labs 3 pagesEricDinh-CMIT321-CEH Module 2.docxEricDinh-CMIT321-CEH Module 2.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2019 Register Now EricDinh-CMIT321-CEH Module 2.docx 6 pagesModule_8,11,13Module_8,11,13 University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now Module_8,11,13 1 pagesCMIT321 Week 7 Discussions ACMIT321 Week 7 Discussions A University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now CMIT321 Week 7 Discussions A 8 pagesCMIT321QUIZ7.pdfCMIT321QUIZ7.pdf University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now CMIT321QUIZ7.pdf 3 pagesCMIT 321 wk3 combined dissCMIT 321 wk3 combined diss University of Maryland, University College Ethical Hacking
CMIT 321 – Spring 2017 Register Now CMIT 321 wk3 combined diss 8 pagesCMIT 321- Module 6 Lab.docxCMIT 321- Module 6 Lab.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now CMIT 321- Module 6 Lab.docx 10 pagesModule 11 – Hacking WebserversModule 11 – Hacking Webservers University of Maryland, University College Ethical Hacking
CMIT 321 – Fall 2016 Register Now Module 11 – Hacking Webservers 19 pagesLab 2 Screenshots.docxLab 2 Screenshots.docx University of Maryland, University College Ethical Hacking
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
CMIT 321 – Summer 2015 Register Now Lab 2 Screenshots.docx 4 pagesCFT Project 1.docxCFT Project 1.docx University of Maryland, University College Ethical Hacking
CMIT 321 – Summer 2015 Register Now CFT Project 1.docx Prev 1 2 3 4 5 Next Recent Documents 4 pagesProject 1 – Rules of Engagement.docxProject 1 – Rules of Engagement.docx University of Maryland, University College
CMIT 321 – Fall 2021 Register Now Project 1 – Rules of Engagement.docx 4 pagesProject 3 – Gaining Access Plan.docxProject 3 – Gaining Access Plan.docx University of Maryland, University College
CMIT 321 – Fall 2021 Register Now Project 3 – Gaining Access Plan.docx 9 pagesProject 4 – Final Penetration Test Proposal.docxProject 4 – Final Penetration Test Proposal.docx University of Maryland, University College
CMIT 321 – Fall 2021 Register Now Project 4 – Final Penetration Test Proposal.docx 5 pagesProject 2 – Reconnaissance and Scanning Plan.docxProject 2 – Reconnaissance and Scanning Plan.docx University of Maryland, University College
CMIT 321 – Fall 2021 Register Now Project 2 – Reconnaissance and Scanning Plan.docx 12 pagesCEH321_Modules 6 7 10.docxCEH321_Modules 6 7 10.docx University of Maryland, University College
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
CMIT 321 – Fall 2021 Register Now CEH321_Modules 6 7 10.docx Ethical Hacking Tests Questions & Answers Showing 1 to 8 of 74 View all This is a file analyzing question. If I download a file [File (.file)]
How can I find the exact name for that file? The machine being used is a windows 10 1 2 3 4 5 how to Identify the exactfile nameand extension if applicable. 1 2 3 4 5 Please refer to the attachment to answer this question. This question was created from Screenshot 2021-07-20 232456.png. 1 2 3 4 5
For one of my practice quizzes, I have copies of registry files contained in a .zip file. I have unzipped them to reveal default, SAM, SECURITY, software, and 1 2 3 4 5 Explain how you approached two of the 10 CTF challenges you… Explain how you approached two of the 10 CTF challenges you attempted and solved. For example, 1 2 3 4 5
For the summer of 1997, what program was on the UMUC cable channel on Monday at 4 PM according to the UMUC Television Programming Schedule? 1 2 3 4 5 Sophos mobile security include ( chose all that apply) privacy protection and security loss and theft protection spam protection antivirus antimalware 1 2 3 4 5
CMIT 321 CMIT321 CMIT/321 Week 4 Discussion
how do I use providedregistryfilesto determine the version of Google Chrome with SAM, security, software and system files that are coded? do I need to open 1 2 3 4 5 Back to Department Related Courses CMIT 425 – (1300 Documents)CMIT 369 – Installing/Configuring Windows Server (1036 Documents)
CMIT 350 – (939 Documents)CMIT 320 – (938 Documents)CMIT 391 – (782 Documents)CMIT 265 – (698 Documents)CMIT 202 – (678 Documents)CMIT 370 – Windows Server 2012 (636 Documents)CMIT 424 – (519 Documents)CMIT 495 – Capstone (514 Documents)